New Bazar Trojan Slips Past Your Email Defenses!

A new trojan appearing in phishing emails is tricking home users into letting hackers enter their computer or home network. A trojan is a specific kind of malware that disguises itself as a legitimate program or email attachment. This new variant of the “Bazar” trojan is equipped with anti-analysis techniques to make it harder to be detected by anti-virus software.
Iranian Cyber Attacks a Threat to Businesses in the Wake of Recent Airstrikes

It is not news that cyber risks are on the rise and attacking businesses every day, but since U.S. airstrikes killed Iranian military official Qasem Soleimani last Friday at Bagdhad’s airport, top intelligence officials are warning of heightened cyber threats from Iran here in the states. Following the strike, the Department of Homeland Security issued a […]
Multi-Factor Authentication: Why it’s Important & Newsworthy

There is no doubt you’ve heard of multi-factor authentication either when signing up for a new online account or when browsing the internet–but what exactly is it and why is it so important? And why is it suddenly making headlines? First, let’s cover what multi-factor authentication is, so you can understand the rest going forward. According to […]
City of Charlottesville Has Experienced Security Breach

A security breach at City Hall in Charlottesville has affected at least 10,700 current and former utility billing customers and their personal information. Sensitive data that was compromised includes customer social security numbers, addresses, and drivers license numbers. The breach was discovered while investigating a completely unrelated phishing scam the city had launched back in May […]
Ransomware, Anyone? Here We Go, Again!
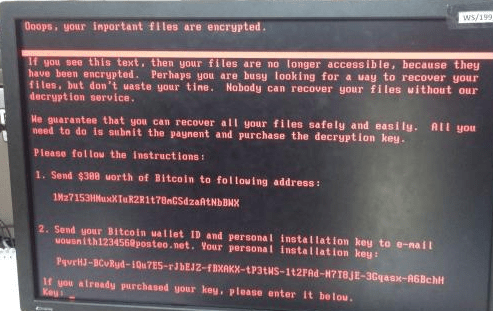
News reports over the past two hours have started showing up from all over the world, reporting that another aggressive ransomware virus is making its way from country to country, primarily in the form of an e-mail attachment. (As usual) This time, it reportedly began as an infected Microsoft Excel data file, which upon execution […]
